2015
Lynda
Jungwoo Ryoo
1:49
English
Network protection is vital to organizations big and small, but it doesn't have to be an expensive proposition. Learn how to protect your network with open-source tools, and do it completely FREE. Jungwoo Ryoo shows how to set up firewalls, investigate network traffic with a packet analyzer, detect threats and malicious activity with an intrusion-detection system, and enable network logging and monitoring. Start here for a low-cost route to a more secure network.
Introduction
Welcome
What you should know before watching this course
1. Understanding Firewalls
What is a firewall?
A host firewall
A network firewall
Static packet filtering (SPF) vs. stateful packet inspection (SPI)
2. Host as a Router
Netfilter and iptables
Using iptables to set up a host firewall
Creating a shell script to automate configuring Netfilter
Understanding hosts as routers
Host as a router: Including an additional network adapter
Host as a router: Setting up a second host to test the router
Host as a router: Setting up IP forwarding
Host as a router: Configuring the router's Netfilter settings
Host as a router: Testing
3. Host as a Firewall
Understanding using a host as a network firewall
Setting up a web server to receive forwarded packets
Configuring port forwarding by adding Netfilter rules
Testing port forwarding
Understanding one-legged demilitarized zones (DMZs) using iptables
Using iptables to set up a one-legged DMZ
Using iptables to set up a true DMZ
Understanding Squid, an application proxy firewall
Setting up Squid
Fine-tuning the Ubuntu router host
4. Packet Analysis
What is a packet analysis?
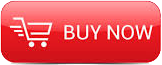
Packet-analysis applications in network security: ARP poisoning example
Packet capturing with Wireshark
Exploring Wireshark's advanced features
Demonstrating Wireshark's advanced features
5. Intrusion Detection Systems (IDS) and Vulnerability Assessment
What is an IDS?
Introducing Snort
Snort as a packet sniffer
Snort as an IDS: Establishing rules
Snort as an IDS: Detecting pings
What is network vulnerability assessment?
Nessus
Network scanning with Nessus
6. Logging and Monitoring
Logging and its significance
Syslog-ng
Log forwarding using syslog-ng: Part one
Log forwarding using syslog-ng: Part two
Kiwi
Simple Network Management Protocol (SNMP)
Conclusion
Next steps
Download File Size:275.02 MB